Email Scams: How to Spot Fake Invoices in Your Email
Cybercriminals are constantly devising new ways to exploit unsuspecting individuals and businesses. One of the most common methods is through fake invoices sent via email. These deceptive messages are designed to trick recipients into paying for goods or services they never ordered or authorized.
Not only do I get these fake invoices sent to me on a weekly basis, but I also answer multiple questions from customers asking about the legitimacy of an email that they have received. 99.99% of the time the invoice is fake.
Let’s look at common signs of fake invoices and provide tips on how to spot them.
Know Who You Do Business With
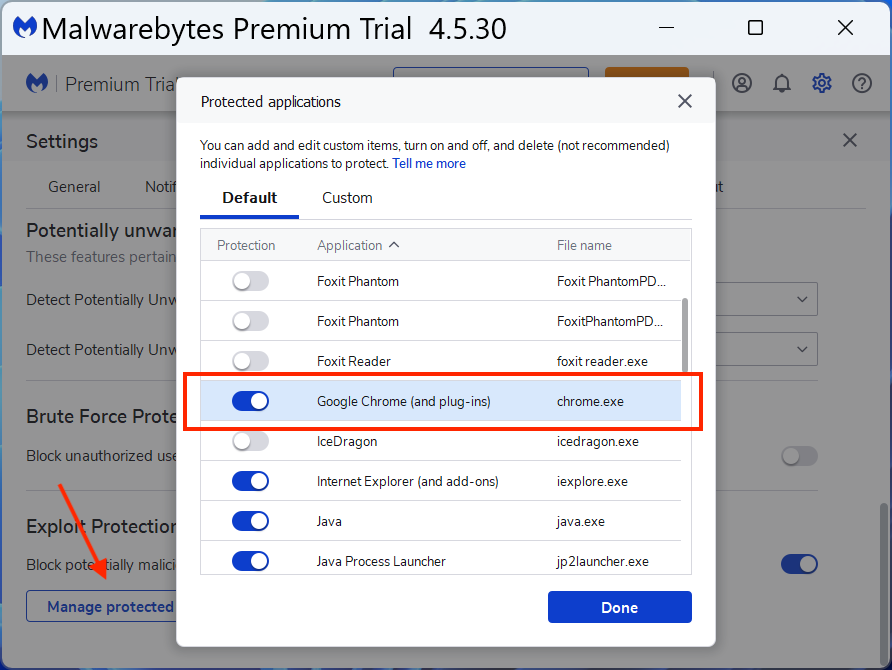
The overwhelming majority of fake invoices have to do with services or products like antivirus that are set to auto-renew unless you take immediate action. If you receive an email like this (along with an attached invoice) ask yourself a couple of questions like: Do I do business with this company? Do I use their product and/or service?
Familiarize yourself with the companies that you do business with and the products or services of theirs that you use. If you receive an invoice claiming to be from McAfee or Norton stating that your antivirus is about to expire, but you use Malwarebytes (which can be purchased through us) to protect your computer you can be sure this is a scam. Delete the email and go happily about your life!
Watch for Generic Emails
One of the first red flags to look out for is a generic or impersonal email. Legitimate invoices often include personalized greetings, recipient details, and specific references to previous transactions and/or account numbers. Fake invoices, on the other hand, tend to lack these personal elements. For instance, an email with a subject line like “Invoice #12345” or a generic salutation like “Dear Customer” should raise suspicion.
The following example was forwarded to me from a customer. Notice that there is no body or subject line, just an attached invoice:
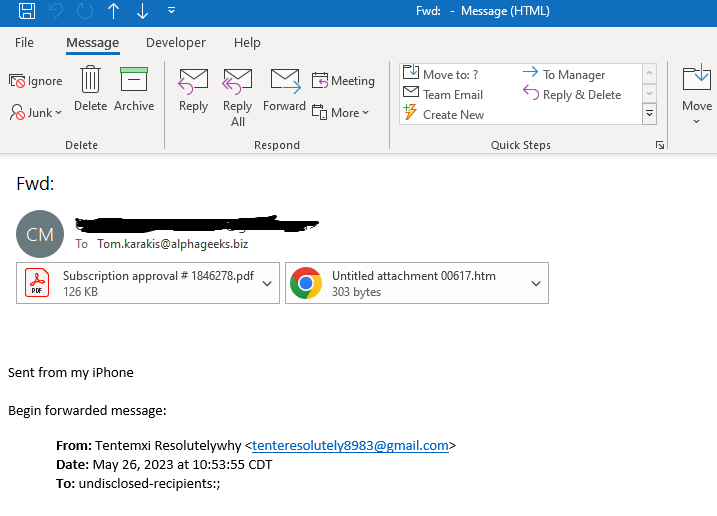
Generic Email. Notice the To and From lines. Not personal and very generic
Examine the Sender’s Email Address
Scammers often use email addresses that resemble legitimate business accounts. However, upon closer inspection, you may notice slight variations or misspellings in the sender’s email address. These subtle differences can be a clue that the invoice is fake. Be cautious of email addresses that include extra numbers, random characters, misspelled domain names, or come from a domain other than the company. Take a look at the following example that was sent to me. Notice that it appears to come from McAfee Support but a couple of things are going on here. For one it actually says McAffee Support (note that McAfee is spelled wrong), and that the ensuing email address does not come from McAfee.com but from a different domain (what is after the @ symbol). Take a look at the previous example as well and you will see it comes from a Gmail address, and not from the company they are purporting to be.
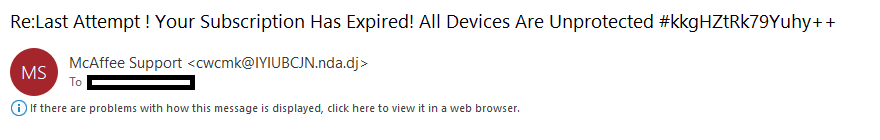
Email address examination
Hover Over Links and Attachments
Fake invoices often contain malicious links or attachments that can compromise your device’s security or lead to phishing websites. Before clicking on any links (which I don’t recommend doing even if you think the email is legit) or downloading attachments, hover your cursor over them to reveal the actual destination. If the URL seems suspicious or does not match the expected website, refrain from interacting with it and delete the email immediately. The following example is from an email I received. I hovered my mouse on the blue “subscription” link and the ensuing box that popped up shows where that link goes to. Notice that it does not go to McAfee.com at all, but rather to a school website (clicking on the picture will open it in a new tab with a larger view. Close tab to return to article.)
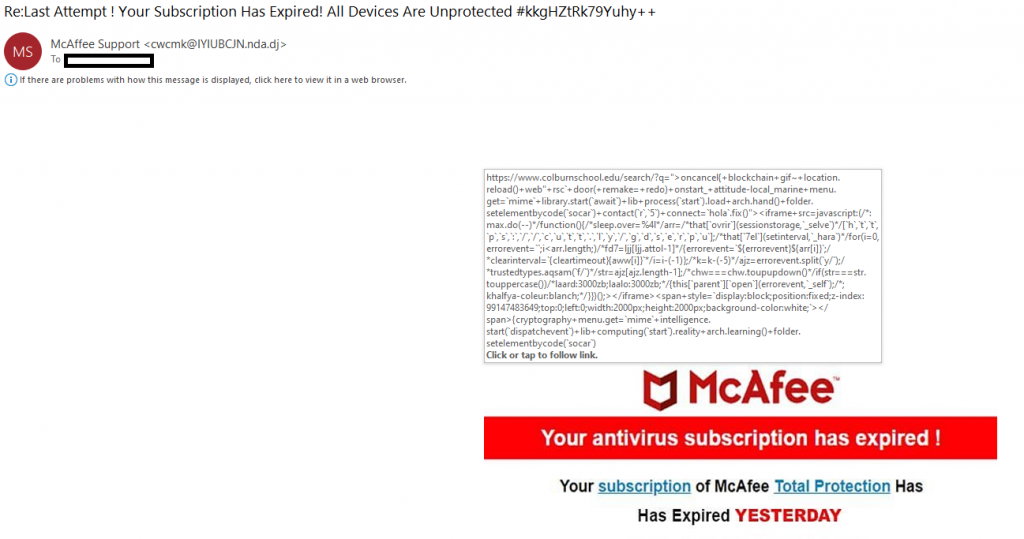
Hovering over a link shows it does not go to Mcafee.com
Miscellaneous Checks
There are a couple of other things you can do if you doubt the legitimacy of an emailed invoice.
- Check for spelling or grammar errors. While it can happen, it would be very doubtful that a company would send out an email containing these types of errors
- DO NOT call any phone numbers in the email or invoice. They are trying any way possible to get you to interact with them so they can steal your money. Any phone number in the email or invoice belongs to the scammer.
- If in doubt go to the companies website by typing it in to a web browser and look for a Log In link. You would have to have an established account with them in order for any invoice to be valid. Try to log in with a user name (usually your email address) and password. If you do not remember a password click on the I Forgot My Password link. Once you are able to successfully log in to your account there should be an area for order history and a place to pay any outstanding invoices
- While on the companies website look for a Contact or Support phone number (do not get this from the email). Any legitimate invoice will have a reference or invoice number. Contact the company and reference the invoice number to ensure that it is valid.
- Use common sense. If it seem “off” trust your gut. It usually is
Conclusion
As cybercriminals become more sophisticated, it’s crucial to stay vigilant and informed about potential scams like fake invoices. By recognizing the signs, such as generic emails, suspicious sender addresses, poor formatting, inaccurate contact information, and suspicious links or attachments, you can protect yourself and your business from financial losses and data breaches. Remember to always double-check the authenticity of an invoice before making any payments or sharing sensitive information. Stay alert, stay informed, and stay secure!